AWS IoT Remote SSH: Secure Access To Your Devices
Is it possible to securely manage and control your Internet of Things (IoT) devices from anywhere in the world? The answer is a resounding yes, and Amazon Web Services (AWS) offers a suite of tools to make it a reality.
In the rapidly evolving landscape of the Internet of Things, the ability to remotely access and manage your devices is no longer a luxury but a fundamental requirement. Whether you're a developer debugging code, an organization monitoring industrial equipment, or a business ensuring the smooth operation of connected devices, the need for secure remote access is paramount.
This article will delve into the capabilities of AWS IoT Remote Access, with a particular focus on how you can leverage Secure Shell (SSH) to connect to your devices securely. We'll explore the benefits, setup process, and best practices, providing you with the knowledge to build robust and reliable IoT solutions tailored to your specific needs.
- Karoline Leavitt Height Facts About Trumps Press Secretary
- Free Iot Setup Raspberry Pi Vpc Ssh On Aws
Let's consider the key aspects of AWS IoT Remote Access:
AWS IoT Remote Access
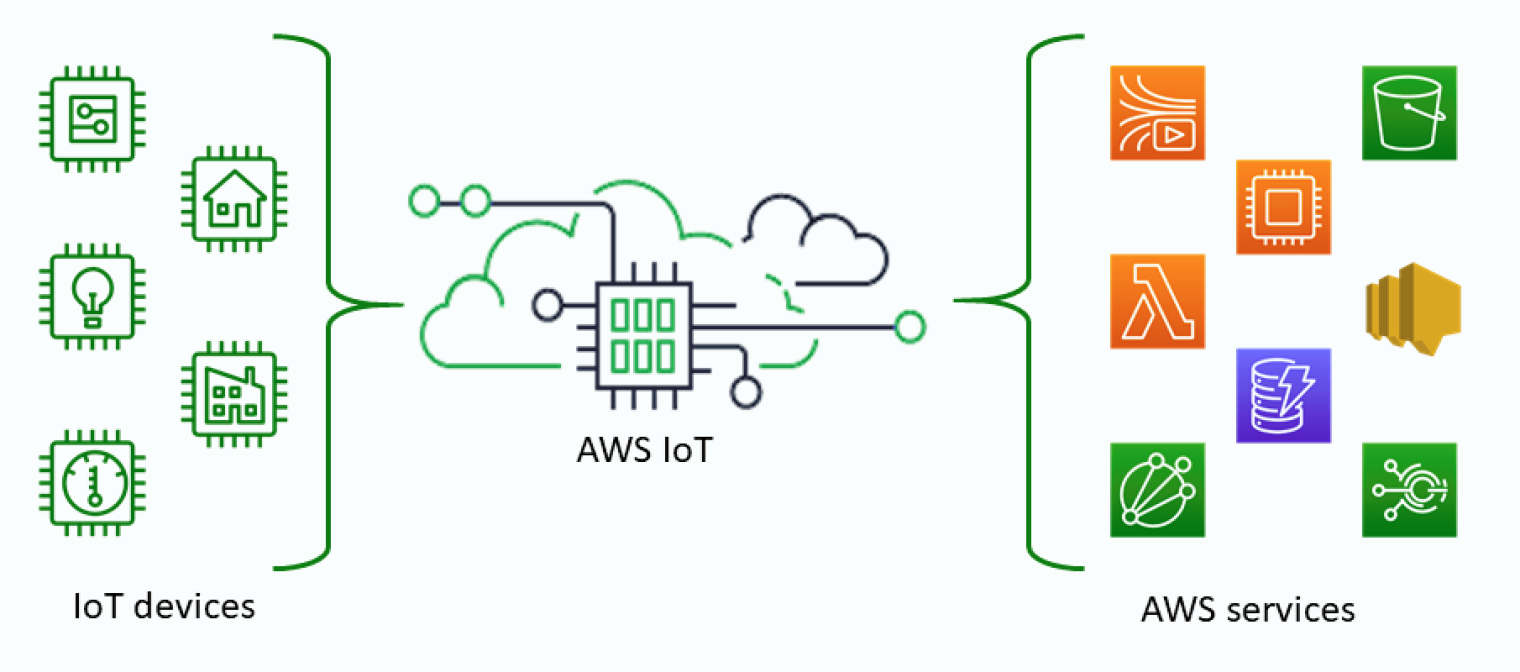
AWS IoT Remote Access offers a robust solution that empowers organizations to seamlessly connect, control, and gather insights from their IoT devices regardless of geographical boundaries. It bridges the gap between convenience and security, allowing you to troubleshoot, monitor, and control your IoT devices from afar. This capability is essential for monitoring, troubleshooting, and maintaining devices without physical presence.
At the heart of AWS IoT Remote Access lies a suite of services designed to facilitate secure communication and device management. These include AWS IoT Core, AWS IoT Device Management, and AWS IoT Secure Tunneling, each playing a crucial role in enabling remote access.
- Exploring Gift Ideas By Genie Free Movie Options Discover Now
- Movierulz Latest Movies Reviews Alternatives To Watch Online
AWS IoT Core acts as a managed cloud service that allows connected devices to interact securely with cloud applications and other devices. This is where your IoT devices connect to the cloud. AWS IoT Device Management offers the tools you need to register, organize, monitor, and remotely manage your fleet of IoT devices at scale. Finally, AWS IoT Secure Tunneling provides a secure, remote access solution that directly integrates with AWS IoT to allow you to access your IoT devices remotely from anywhere.
To open a tunnel using this method, you must have created an IoT thing in the AWS IoT registry. For example, "remotedevicea".
The Power of Secure Tunneling
Secure tunneling is a game-changer for remote IoT device access. Using secure tunneling to establish bidirectional communication to remote devices over a secure connection that is managed by AWS IoT. It provides a secure, remote access solution that directly integrates with AWS IoT. This means that you can access your IoT devices remotely from anywhere.
One of the key advantages of secure tunneling is its ability to bypass the need for updates to your existing inbound firewall rules. This keeps the same security level provided by firewall rules at a remote site without adding operational overhead. You can open a secure tunnel using the AWS Management Console, the AWS IoT API reference, or the AWS CLI.
The use case for secure tunneling can be many, such as debugging or remedy device anomalies, and more. Thats exactly what AWS IoT Remote SSH offers.
AWS IoT Secure Tunneling creates a secure tunnel to your IoT device (destination device) and carries out remote operations over SSH. The integration of SSH on AWS enhances this process by providing a secure communication channel. Furthermore, AWS offers a scalable and secure infrastructure that allows businesses to deploy IoT devices globally while keeping them under control.
In the modern digital era, remote IoT VPC SSH access through AWS has become an essential tool for developers and organizations looking to securely manage their IoT devices from anywhere in the world.
By leveraging AWS's robust infrastructure, users can achieve seamless connectivity and enhanced security for their IoT ecosystems.
When using AWS IoT Secure Tunneling, the device might get disconnected unexpectedly even if the tunnel is open. A device can get disconnected for multiple reasons. The aws iot device management SLA stipulates that you may be eligible for a credit towards a portion of your monthly service fees if aws iot device management fails to achieve a monthly uptime percentage of at least 99.9% for aws iot device management.
If you want to deliver the destination client access token to the remote device through methods other than subscribing to the reserved MQTT topic, you might need a destination client access token (CAT) listener and a local proxy.
If you want to deliver the destination client access token to the remote device through methods other than subscribing to the reserved MQTT topic, you might need a destination client access token (cat) listener and a local proxy.For more information on AWS IoT Core, see what is AWS IoT?.For more information on AWS IoT Device Management jobs, see what is AWS IoT Jobs
Setting Up IoT Remote Access with SSH
Setting up IoT remote access with SSH on AWS involves several steps, from configuring devices to securing connections.
To get started, you'll need an IoT device agent running on the remote device that connects to the AWS IoT Device Gateway and is configured with an MQTT topic subscription. You can use the quick setup method to rotate the access tokens and SSH into the remote device within the browser. You can optionally configure a destination name, but it's not required for this tutorial.
Before you begin, ensure that your IoT device is registered with AWS IoT Device Management. You can register new devices with AWS IoT Device Management.
Key Components of AWS IoT Remote Access
AWS provides several services tailored for IoT remote access, including:
- AWS IoT Core: A managed cloud service that allows connected devices to interact securely with cloud applications and other devices.
- AWS IoT Device Management: This suite offers tools to register, organize, monitor, and remotely manage your fleet of IoT devices at scale.
- AWS IoT Secure Tunneling: This provides a secure, remote access solution that directly integrates with AWS IoT, allowing you to access your IoT devices remotely from anywhere.
Best Practices for Secure Remote Access
Implementing secure remote access requires a multifaceted approach. Here are some best practices to consider:
- Use Strong Authentication: Employ robust authentication methods, such as multi-factor authentication (MFA), to verify user identities.
- Regularly Rotate Credentials: Rotate access tokens and other credentials frequently to minimize the impact of potential compromises.
- Implement Least Privilege: Grant only the necessary permissions to users and devices. Limit access to the minimum required for their tasks.
- Monitor and Audit: Continuously monitor access logs and audit configurations to detect and respond to suspicious activity.
- Keep Software Updated: Regularly update the operating systems, software, and agents on your IoT devices to patch vulnerabilities.
- Secure Network Configuration: Use firewalls, VPNs, and other network security measures to protect the communication between your devices and the AWS cloud.
Troubleshooting Common Issues
Even with careful planning, you may encounter issues. Here are some common problems and their solutions:
- Device Disconnections: Devices may disconnect unexpectedly for multiple reasons, including network instability or configuration errors. Ensure a stable network connection and verify device configurations.
- Token Rotation Failures: Verify that the token rotation mechanism is correctly implemented and that devices have the necessary permissions to rotate access tokens.
- Firewall Restrictions: Ensure that your firewall rules allow communication between your devices and the AWS IoT services.
- Access Denied Errors: Review your IAM policies and ensure that users and devices have the necessary permissions to access the required resources.
In this blog, you learned how to use this AWS IoT device management feature to gain access to remote devices from a web application.
AWS IoT services for remote access offers a robust solution that empowers organizations to seamlessly connect, control, and gather insights from their IoT devices regardless of geographical boundaries.
By tapping into the capabilities of the AWS IoT platform and following best practices for security and performance, businesses can build scalable and reliable IoT solutions tailored to their needs.

Detail Author:
- Name : Dr. Lennie O'Keefe
- Username : meichmann
- Email : leonie.bartell@yahoo.com
- Birthdate : 1991-02-09
- Address : 472 Ledner Overpass Suite 778 New Abbie, WY 43234
- Phone : +14156218629
- Company : Cronin Ltd
- Job : Urban Planner
- Bio : Aut facere dolorem quaerat rerum quia eaque. Enim repellat accusantium voluptatem voluptate dignissimos sed unde.
Socials
linkedin:
- url : https://linkedin.com/in/nellesawayn
- username : nellesawayn
- bio : Nisi sapiente hic id nihil maiores labore.
- followers : 2567
- following : 1074
twitter:
- url : https://twitter.com/nelle_real
- username : nelle_real
- bio : Laudantium similique officiis numquam eos. Cupiditate perspiciatis minima ipsa nisi. Fuga quod et fuga non culpa qui. Ea officiis architecto vitae ea eos.
- followers : 1824
- following : 321
tiktok:
- url : https://tiktok.com/@nelle.sawayn
- username : nelle.sawayn
- bio : Voluptatem fugit beatae sed odit veritatis. Sed debitis quis est voluptatem.
- followers : 5174
- following : 2874