SSH Into Raspberry Pi: Your Ultimate Guide
Can you truly harness the power of your Raspberry Pi, even when you're miles away? The answer lies in SSH, a secure gateway that unlocks remote access and control, transforming your tiny computer into a global command center.
The digital landscape offers an abundance of possibilities for the modern maker and enthusiast. One of the most powerful tools in this arena is the Raspberry Pi, a versatile single-board computer. However, its true potential is often realized not just by what it can do, but by how easily you can access and control it. That's where Secure Shell, or SSH, comes into play. This technology allows you to connect to your Raspberry Pi remotely, from almost anywhere in the world, providing a secure and flexible way to manage your projects, access your data, and troubleshoot any issues that arise.
Before diving into the specifics, let's clarify the fundamentals. SSH is a network protocol that establishes a secure channel between two devices. This means all communication is encrypted, protecting your data from prying eyes. When you use SSH with your Raspberry Pi, you are essentially creating a secure tunnel, allowing you to execute commands, transfer files, and interact with your Pi's operating system as if you were sitting right in front of it.
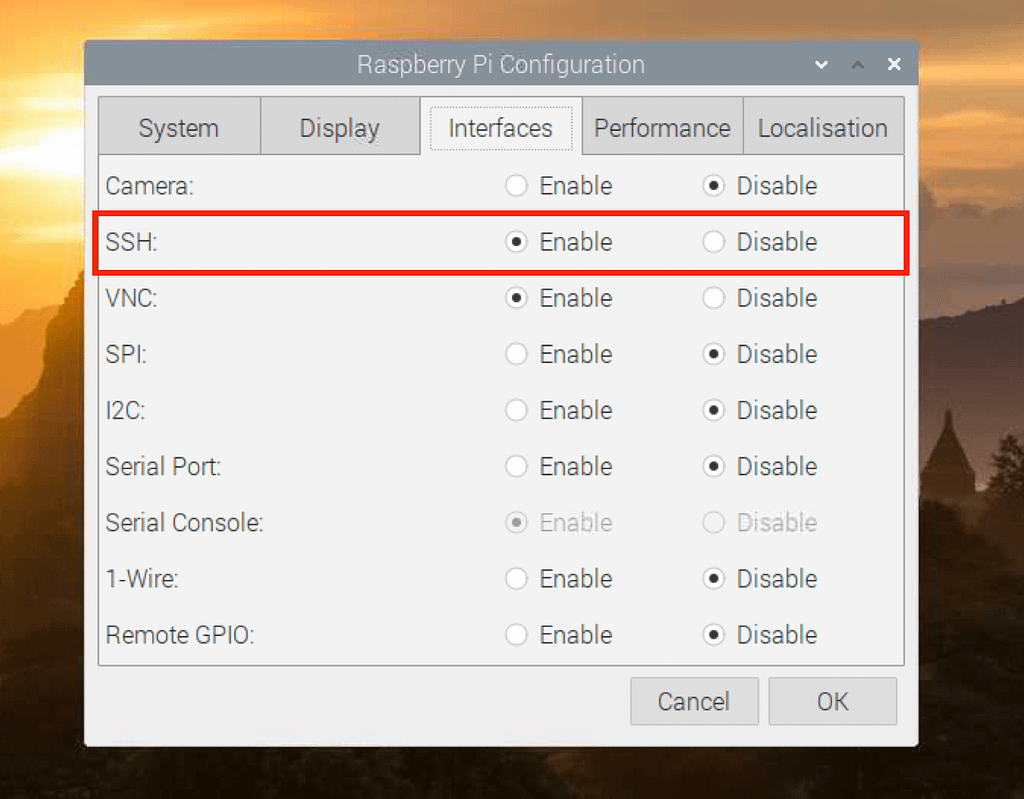
Now, let's look at how you can turn on and configure SSH on your Raspberry Pi. The process varies slightly depending on your setup, but the core steps remain consistent.
| Feature | Details |
|---|---|
| Enabling SSH (Graphical Interface) |
|
| Enabling SSH (Command Line) |
|
| Finding Your Raspberry Pi's IP Address |
|
| Connecting via SSH (Local Network) |
|
| Connecting via SSH (External Network) |
|
Setting up SSH is often a simple matter of enabling it in the Raspberry Pi configuration tool, then using an SSH client like PuTTY (Windows) or the built-in terminal (macOS/Linux) to connect. The username is typically "pi", and the default password is "raspberry". However, it's strongly recommended that you change the default password immediately after enabling SSH to protect your device from unauthorized access.
Beyond the basics, SSH offers a wealth of functionality: file transfer, remote command execution, and secure tunnel creation are just a few examples. Secure Copy (SCP) and Secure FTP (SFTP) are two methods for transferring files, using the same secure channel as SSH. You can use the `scp` command in the terminal for command-line file transfers or utilize graphical SFTP clients like FileZilla.
- Decoding Palang Tod Meaning Series More Your Guide
- Secure Remote Iot Raspberry Pi Aws Vpc Windows Download
For advanced users, SSH also supports port forwarding. This allows you to create secure tunnels to access services running on your Raspberry Pi, like web servers or databases, even from outside your local network. Port forwarding can be used to forward a specific port on your local machine to a port on the Raspberry Pi. The Raspberry Pi becomes a gateway, allowing you to securely access resources on your home network.
Let's address some specific scenarios and potential pitfalls.
| Problem | Solution/Explanation |
|---|---|
| Unable to connect via SSH on the local network. |
|
| Unable to connect via SSH from outside the local network. |
|
| SSH connection times out. |
|
| "Connection refused" error. |
|
Beyond the traditional methods, there are alternative approaches for remotely accessing your Raspberry Pi, each with their pros and cons. These options often offer increased security and simplify the connection process.
| Method | Description | Pros | Cons |
|---|---|---|---|
| Virtual Private Network (VPN) |
|
|
|
| Cloud-Based Remote Access Services (e.g., RealVNC, Remote.it) |
|
|
|
| Raspberry Pi Connect |
|
|
|
For a more secure and user-friendly experience, consider using a VPN. Setting up a VPN on your Raspberry Pi creates an encrypted tunnel between your device and your home network. This allows you to connect to your Raspberry Pi securely, as if you were physically present at home. PiVPN is a popular option, which simplifies the process of setting up OpenVPN or WireGuard on a Raspberry Pi.
For users seeking a simpler setup, cloud-based remote access services such as RealVNCs cloud VNC viewer or remote.it can streamline the connection process. These services eliminate the need for complex port forwarding configurations by providing a secure connection through their servers. This is especially beneficial if you have a dynamic IP address or limited technical expertise. Raspberry Pi Connect offers a similar service specifically for Raspberry Pi devices.
Security is paramount when enabling remote access. Always change the default password for the "pi" user immediately after enabling SSH. Consider using key-based authentication instead of passwords, which is more secure. Disable password authentication altogether if feasible and always keep your Raspberry Pis operating system and software up to date to patch any security vulnerabilities.
No matter which method you choose, understanding the fundamentals of SSH and remote access empowers you to control your Raspberry Pi from anywhere in the world. The ability to remotely access your device unlocks a new level of convenience and functionality, making your Raspberry Pi projects even more useful and accessible.
In essence, SSH transforms your Raspberry Pi into a versatile tool, opening up a world of possibilities for remote access and control. By following these guidelines and staying mindful of security best practices, you can confidently harness the power of your Raspberry Pi, wherever you may be.
Detail Author:
- Name : Estefania Braun
- Username : baby75
- Email : ogreenholt@steuber.com
- Birthdate : 1995-06-22
- Address : 450 Emile Junctions Suite 633 West Skylaberg, ID 07419-0285
- Phone : (281) 664-7705
- Company : Bogan, Yundt and Feest
- Job : Restaurant Cook
- Bio : Neque voluptas accusamus possimus possimus blanditiis ipsa. Aliquam ut placeat quidem sit vel dolore.
Socials
twitter:
- url : https://twitter.com/erickreynolds
- username : erickreynolds
- bio : Illum autem sed minima eos cupiditate. Cumque qui corrupti sed odit modi. Sit officiis eos quaerat.
- followers : 1214
- following : 757
instagram:
- url : https://instagram.com/erick_xx
- username : erick_xx
- bio : Ipsum ut voluptas et debitis. Deserunt quia ut rerum ut. Voluptas vel nesciunt laudantium odio.
- followers : 4283
- following : 71
tiktok:
- url : https://tiktok.com/@erick.reynolds
- username : erick.reynolds
- bio : Cumque minima est et est sequi reprehenderit.
- followers : 2322
- following : 187
facebook:
- url : https://facebook.com/erick1426
- username : erick1426
- bio : Labore qui nobis adipisci labore iste.
- followers : 1769
- following : 351