SSH To IoT Devices: Secure Remote Access With AWS & Windows 10
Can you imagine a world where you can effortlessly manage and monitor your Internet of Things (IoT) devices from anywhere, anytime? The answer is a resounding yes, and it's achievable through a secure and efficient method involving Secure Shell (SSH) and the power of cloud services like Amazon Web Services (AWS).
The landscape of remote device management has dramatically shifted, driven by the exponential growth of IoT devices. From smart homes and industrial sensors to remote servers, the need for secure, reliable, and accessible connections is paramount. SSH, a cornerstone of secure remote access, steps in as a robust solution, and when combined with AWS, it unlocks a new level of control and efficiency.
Setting up remote SSH access to your IoT devices using AWS involves several key steps. The process, while potentially appearing complex at first glance, becomes surprisingly manageable when broken down into logical phases. This guide will walk you through each step, ensuring that you can establish a secure and reliable connection that meets your specific needs. Whether you're a seasoned IT professional or just starting to explore the world of IoT, the knowledge you gain here will empower you to manage your devices with confidence.
- Download Remoteiot Web Ssh Your Ultimate Guide Tips
- Teri Hatcher Lois Lane More A Look At Her Iconic Roles Discover
AWS plays a pivotal role in this equation, acting as a central hub for your IoT devices. This allows them to communicate securely with the cloud. With this setup, you gain the ability to manage device fleets, update firmware, and monitor device healthall from a single, unified dashboard. This centralized control significantly simplifies device management, reducing the complexities and costs associated with on-site troubleshooting and maintenance. The combination of SSH and AWS is like a carefully crafted symphony of technologies, all working in harmony to bring you unparalleled control over your IoT ecosystem.
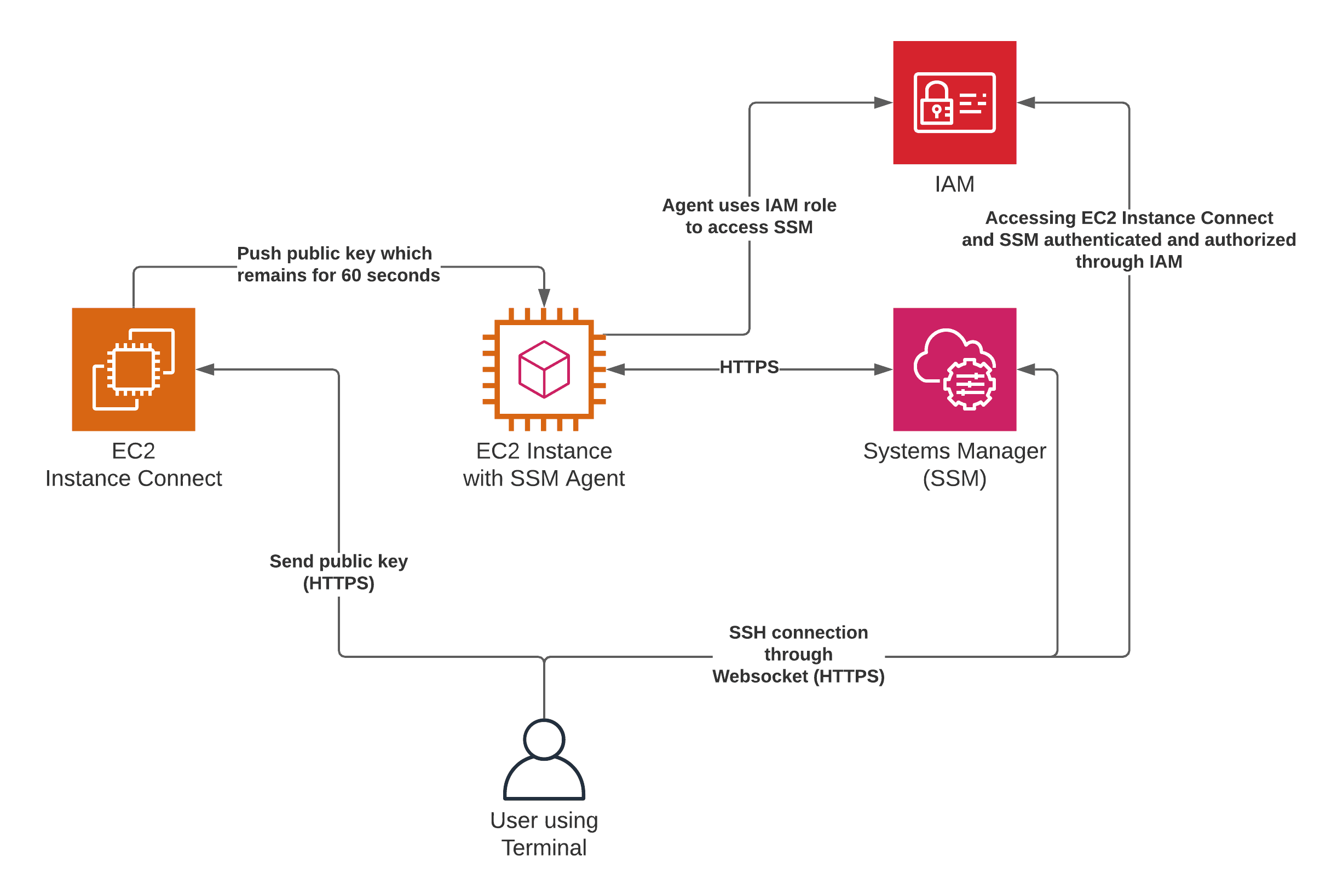
Connecting to an IoT device over the internet using SSH via AWS on a Windows machine may initially appear daunting. However, with the right tools and knowledge, the process is entirely achievable. This guide is designed to walk you through the setup of an EC2 instance, configuration of security groups, and the establishment of an SSH tunnel, allowing you to securely manage your IoT devices from any location globally. This method provides an added layer of security, with encrypted data transfer and improved control over the remote devices.
This approach is a modern solution for accessing devices that are behind firewalls, or simply inaccessible over the internet. This involves using a secure tunnel to create bidirectional communication to remote devices over a secure connection managed by AWS IoT. The best part is that this method does not require updates to your existing inbound firewall rules, which allows you to keep the same security level provided by firewall rules at a remote site.
- Bryant Ac Systems Costs Lifespan More Your City Guide
- Best Free Iot Ssh P2p Secure Remote Access Raspberry Pi
The benefits are clear: enhanced security, encrypted data transfer, and improved control, all of which contribute to a more robust and manageable IoT infrastructure. Compared to other remote access methods, SSH offers a higher level of protection, crucial for managing sensitive data transmitted by IoT devices. This also eliminates the need for sending technicians on-site to connect to devices, thereby reducing complexity and costs of device management. AWS also offers a range of IoT offerings, but if you are not using AWS, you can take a traditional approach of using SSH with a VPN or a proxy connection.
This tutorial will cover the essentials, breaking down each stage into easy-to-follow steps. We'll install Putty, configure SSH on your IoT devices, and ensure seamless communication and control in no time. Whether you're managing smart home devices, industrial sensors, or remote servers, this guide will equip you with the knowledge to establish a secure and efficient connection. Lets dive into the fascinating world of IoT and see how to bring these devices within your grasp.
The core principle is straightforward: use SSH to create a secure, encrypted channel to your IoT devices, allowing you to manage them as if you were on the same local network. This is achieved by leveraging the power of SSH, setting up a virtual network, and employing AWS services to facilitate secure and reliable communication. The process typically involves setting up an EC2 instance, configuring security groups, establishing an SSH tunnel, and then accessing the IoT device through this secure channel.
Imagine the possibilities. You're on vacation, but you need to update the firmware of a critical sensor in your factory. Or perhaps you need to troubleshoot a smart home device from the comfort of your couch. With SSH over AWS, these scenarios become reality, offering unparalleled control and flexibility. Whether you are working with Windows or Mac, the power of the cloud allows you to create efficient, secure connections between your devices and the outside world.
To connect to your IoT devices via SSH on AWS, youll need several elements: an active AWS account, an IoT device registered within AWS IoT Core, and properly configured SSH keys for secure access. AWS IoT Core acts as a central point for device management, firmware updates, and device health monitoring. This central point also offers a communication layer for devices to connect to the internet and interact with AWS services.
Before delving into the implementation details, let's highlight why SSH is such a valuable tool in the IoT world. SSH, or Secure Shell, is like the Swiss Army knife of remote access tools. It provides a secure and encrypted way to communicate with your devices, crucial when dealing with sensitive data. The benefits are considerable: enhanced security, encrypted data transfer, and improved control over your devices. Troubleshooting becomes less complicated, as it eliminates the need to send technicians on-site. This reduces the complexity and the overall costs associated with the maintenance of the device.
The process of connecting to an IoT device over the internet using SSH involves several key steps, including setting up your IoT device, configuring your network, and utilizing the right tools on your Windows machine. In this guide, we will walk you through each step to provide a comprehensive and easy to follow manual. This will include installing Putty, configuring SSH on your IoT device. We will also cover the core aspects of setting up an EC2 instance, configuring security groups, and establishing an SSH tunnel.
To connect to your local device, use the command that is suitable for your operating system. For example, on the Windows command prompt, you can use `ssh`. You may need to install an SSH client like PuTTY. You'll also need the IP address of your IoT device and the appropriate login credentials. You can run the following command in a terminal window on your computer, replacing `username` and `ip` with the relevant information. For example, if your IP address is 10.143.90.2 and your username is jayesh, the syntax to connect to a remote server is `ssh jayesh@10.143.90.2`.
This method of using secure tunneling does not require updates to your existing inbound firewall rules, ensuring you can keep the same level of security provided by the firewall. Aws offers a range of IoT offerings, but a more traditional approach is possible using SSH with a VPN or proxy connection. All these considerations work together to enhance the experience of accessing the IoT devices from anywhere. This guide will show you the tools, methods, and best practices to set up and access your devices remotely.
Now, lets walk through a step-by-step guide to make this a reality:
1. Setting Up an EC2 Instance: An EC2 instance serves as a secure entry point to your network. You'll choose an instance type based on your needs (e.g., a t2.micro for basic use) and select an appropriate Amazon Machine Image (AMI), such as Amazon Linux 2. When configuring the instance, set up the security group to allow SSH (port 22) access from your IP address.
2. Configuring Security Groups: Security groups act as virtual firewalls for your EC2 instance, controlling inbound and outbound traffic. The security group should be configured to allow SSH traffic on port 22 from your IP address or a specific range. This ensures that only authorized users can access your instance.
3. Generating SSH Keys: You'll need an SSH key pair (a public key and a private key) to securely connect to your EC2 instance. The private key is stored on your local machine and should be kept confidential. The public key is added to the authorized_keys file on the EC2 instance. Create the key pairs using tools like `ssh-keygen` on Linux or macOS, or PuTTYgen on Windows.
4. Setting Up the SSH Tunnel: This is where the magic happens. The SSH tunnel creates an encrypted connection between your local machine and the EC2 instance. From there, you can tunnel traffic to your IoT device. On your local machine, use the command `ssh -L [local_port]:[iot_device_ip]:22 [ec2_user]@[ec2_public_ip]`. This command forwards traffic from a local port to the SSH server (EC2 instance), which then forwards it to your IoT device.
5. Connecting to Your IoT Device: Once the tunnel is established, you can connect to your IoT device via SSH by using `ssh -p [local_port] [username]@[localhost]`. Replace `[local_port]` with the port you specified in the tunnel setup and `[username]` with the username of your IoT device. If you're using Windows, use an SSH client like PuTTY to establish the connection.
6. Installing and Configuring PuTTY (Windows): PuTTY is a popular SSH client for Windows. Download and install it. In PuTTY, enter the EC2 instance's public IP address or hostname and port 22 (or the port you configured for SSH). Under "Connection" -> "SSH" -> "Auth", browse for your private key file (.ppk file) and click "Open" to connect. When connecting to the EC2 instance, use the same user credentials you use for accessing the server.
7. Configuring SSH on Your IoT Device: Ensure that SSH is enabled on your IoT device. This typically involves installing an SSH server package, such as OpenSSH server. Verify that the device is reachable on your network, either through a static IP address or DHCP with a reserved IP. Once you set up this, you can then proceed to accessing your device remotely using the established tunnel.
By following these steps, you can establish a secure and efficient connection to your IoT devices, giving you a great degree of control over your devices. With each step, you build a foundation for a robust system, and with the right skills, you can manage and monitor your devices with ease.
Below is a table summarizing the core elements and providing links to trusted sources for further details:
| Aspect | Description | Details |
|---|---|---|
| EC2 Instance | A virtual server in AWS that acts as a secure entry point. | Select an appropriate instance type and AMI. Configure security groups to allow SSH traffic. |
| Security Groups | Virtual firewalls that control inbound and outbound traffic to the EC2 instance. | Allow SSH (port 22) access from your IP address. |
| SSH Keys | Used for secure authentication. | Generate a key pair (public and private keys) and secure access to your EC2 instance. |
| SSH Tunnel | Creates an encrypted connection between your local machine and the EC2 instance. | Use the `ssh -L` command to forward traffic. |
| IoT Device | The device you want to manage remotely. | Make sure SSH is enabled and configure the device to be on the network |
| SSH Client | The software you use to connect to the EC2 instance and the IoT device. | Examples: PuTTY (Windows), Terminal (macOS, Linux). |
AWS EC2 Documentation
This approach is a comprehensive solution for setting up remote access, and each component works in sync to ensure secure and effective control. By setting up the EC2 instance, you create a secured access point; with security groups, you ensure that unauthorized access is prevented; with SSH keys, you provide a secure authentication mechanism; and by setting up an SSH tunnel, you ensure a secure connection for your data transfer. With the knowledge and skills, the remote device management challenges are eliminated.


Detail Author:
- Name : Yasmine Champlin
- Username : herminio93
- Email : karley26@hotmail.com
- Birthdate : 1973-12-01
- Address : 985 Torp Plaza Apt. 456 Deontown, NE 63698-5779
- Phone : 360.916.5529
- Company : Jacobi, Shanahan and Ferry
- Job : Hazardous Materials Removal Worker
- Bio : Qui perspiciatis velit odit tempore distinctio doloremque. Corporis tempore vitae accusantium et molestiae aliquid. Occaecati at dolores cumque deserunt.
Socials
linkedin:
- url : https://linkedin.com/in/mortimer4299
- username : mortimer4299
- bio : Est veritatis ut ducimus veniam ipsam nobis.
- followers : 6704
- following : 2087
instagram:
- url : https://instagram.com/mortimerbode
- username : mortimerbode
- bio : Iusto sequi sequi corporis id. Nihil quo qui eveniet modi maiores.
- followers : 769
- following : 2513
twitter:
- url : https://twitter.com/bode2015
- username : bode2015
- bio : Quae accusantium qui eius. Qui omnis repellendus illo rem enim. Quaerat ullam et consequatur enim ut commodi ut delectus.
- followers : 5150
- following : 1899
tiktok:
- url : https://tiktok.com/@mortimer_bode
- username : mortimer_bode
- bio : Accusamus sit corporis sapiente in labore. Nam debitis autem porro in totam.
- followers : 922
- following : 1004
facebook:
- url : https://facebook.com/bodem
- username : bodem
- bio : Deleniti eius qui odit excepturi consectetur.
- followers : 339
- following : 1099