Secure IoT: Master Remote SSH Access & Device Management Guide
Are you seeking to remotely manage your Internet of Things (IoT) devices securely and efficiently? The ability to harness Secure Shell (SSH) for your IoT devices empowers you to maintain control, reduce risks, and optimize operations, regardless of physical location.
In an era defined by interconnected devices, the importance of securing and managing these devices cannot be overstated. This comprehensive guide, meticulously crafted, delves into the intricate world of remote SSH access for IoT devices, offering a roadmap to safeguard your network and streamline device management. From the fundamentals of SSH to advanced configurations, troubleshooting tips, and addressing frequently asked questions, we provide the knowledge and skills necessary to navigate this complex landscape with confidence.
Before delving into the specifics, its crucial to understand the core principles underpinning SSH and its significance within the IoT ecosystem. SSH, or Secure Shell, is a cryptographic network protocol designed to securely establish a channel over an unsecured network. It allows for secure remote access to devices, facilitating command execution, file transfer, and other administrative tasks. In the context of IoT, where devices are often deployed in remote locations or on networks with inherent vulnerabilities, SSH emerges as a vital tool for securing and managing these devices.
- Best Iot Platforms With Free Ssh Secure Remote Access Guide
- Loral Infallible Concealer Full Coverage Waterproof Find Out
Consider the ramifications of an unsecured IoT router. As the gateway for multiple connected devices, it becomes a prime target for cyberattacks. Without SSH, your router becomes vulnerable to unauthorized access, potentially leading to data breaches, network compromise, and significant operational disruptions. Setting up SSH on your IoT router is thus not merely a suggestion; it is an imperative step to enhance network security and ensure the integrity of your connected devices. This is a fundamental consideration to ensure your devices are protected.
This guide provides a deep dive into the process of setting up SSH on IoT devices and routers, encompassing every aspect from basic configurations to advanced implementations. The following table provides a structured overview of essential components to master this field.
| Component | Description | Importance |
|---|---|---|
| SSH Protocol | A cryptographic network protocol for secure communication. | Ensures secure remote access and data transfer. |
| IoT Device/Router | The target devices for SSH configuration. | Requires SSH enabled to allow remote access. |
| SSH Client | Software used to connect to the IoT device/router. | Allows secure command execution and management. |
| Port Forwarding | Configuring the router to forward SSH traffic. | Enables remote access from outside the local network. |
| Firewall Configuration | Adjusting firewall settings for SSH access. | Controls incoming and outgoing SSH connections. |
| Key-Based Authentication | Using cryptographic keys for authentication. | Enhances security by eliminating password-based logins. |
Reference: Example SSH IoT Guide
- Movierulz Latest Movies Reviews Alternatives To Watch Online
- Is Adam Ruzek Leaving Chicago Pd What We Know
The benefits of employing SSH for IoT device management are multifaceted. Remote access allows you to monitor, configure, and troubleshoot devices without physical presence, reducing downtime and operational costs. With remote access, you are no longer tethered to the location of your devices, enabling you to address issues promptly and proactively.
This guide meticulously outlines the steps involved in installing IoT device management software on your Linux server, including exploring various software solutions and considering critical factors like device compatibility, ease of use, and feature sets. By mastering these techniques, you will be well-equipped to ensure the security and streamline the operation of your devices, regardless of location. We will navigate the essential steps, covering the following core tasks.
- Ensure SSH is Enabled: The foundation of your SSH setup is to ensure SSH is active on your IoT device. Many IoT devices, especially those running Linux-based systems like Raspberry Pi, have SSH pre-installed but disabled by default. Activating it is a straightforward process, often involving enabling the SSH service through the device's configuration interface.
- Prepare Your Device: Preparing your IoT device for SSH access involves setting up a secure configuration. This includes changing the default password (a critical security step) and setting up a strong username/password combination. The more security precautions you employ, the more safe you and your devices will be.
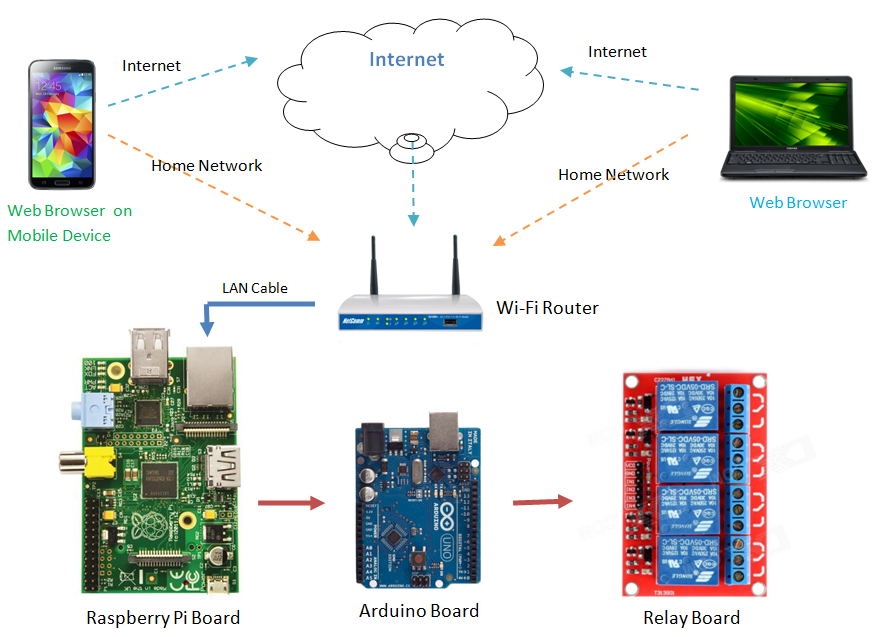
Understanding the intricacies of setting up remote SSH for your IoT devices behind a router is essential. The steps outlined here will provide a complete understanding of your network security. First, you'll need to configure an SSH client on your Windows 10 machine, configure port forwarding on your router, and ensure your IoT device is accessible. This process, when completed, is your base of access to any IoT device.
The process of establishing secure access through SSH is comprised of distinct steps. Here are the key elements:
- Set up SSH client: It's essential to establish an SSH client to connect to your IoT devices.
- Configure Port Forwarding: The second critical element involves configuring port forwarding on your router. This directs incoming SSH traffic to your target IoT device, enabling secure remote access.
- Ensure Device Accessibility: Lastly, ensure your IoT device is accessible.
One of the crucial aspects we will explore is how to implement secure SSH access for IoT devices behind a router. This is particularly important because these devices often serve as gateways for many connected devices, making them prime targets for cyberattacks. Without SSH, your IoT router is vulnerable to unauthorized access, which could lead to data breaches or even complete network compromise. In this guide, you will get complete access on how to set up an SSH client on your Windows 10 machine.
For a more secure configuration, key-based authentication is an advanced method of accessing your devices. It replaces password-based logins with cryptographic keys, which are far more secure. This is an important configuration that makes your devices nearly impossible to hack.
To connect to your IoT device using an SSH client, youll typically use the following command. Replace `username` with your IoT device's username and `your_iot_device_ip` with the device's IP address:
ssh username@your_iot_device_ip
Another aspect we will cover is how to set up SSH for IoT devices. You can easily set up SSH for your IoT devices by following several key steps, including enabling SSH on the device and configuring your network. Its necessary to fully grasp what the device is and how to configure it.
In today's interconnected world, managing SSH IoT devices behind a router has become a critical skill for tech enthusiasts, IT professionals, and home users alike. As the Internet of Things (IoT) continues to expand, understanding how to configure and secure these devices through SSH is essential. Remote SSH access is crucial for managing IoT devices efficiently, especially when they are located in remote locations.
The benefits extend beyond security, offering a way to streamline device management and improve your efficiency. Remote SSH access lets you stay in control, reduce downtime, and improve your IoT device management by eliminating the need to be physically near your device. When it comes to remote device access, it can be difficult to know where to start. You'll need to set up an SSH client on your Windows 10 machine, configure port forwarding on your router, and ensure your IoT device is accessible. In this guide, we delve into the essentials of remote access via SSH without setting port forwarding in your router, enabling you to fully utilize your Linux device.
Furthermore, we will delve into the complexities of setting up your Linux server for remote SSH access and setting up your Raspberry Pi. Before you can remotely access your Linux server, you need to make sure that it is set up correctly. This involves tasks such as installing an SSH server, configuring the firewall, and ensuring the server is accessible on the network. By ensuring these things, you can access and configure your devices from anywhere. With your router and SSH server configured, you can now connect to your IoT devices using an SSH client.
Ultimately, this guide serves as a comprehensive resource, empowering you with the knowledge and tools to securely and effectively manage your IoT devices through SSH. By following the steps outlined in this article, you will gain complete control and be able to troubleshoot your devices with ease. Setting up SSH on IoT devices and routers is an essential step for anyone looking to enhance their network security and streamline device management. Ssh offers a way to safeguard your devices from unauthorized access, while also enabling you to manage them efficiently. By the end of this guide, you will have the skills to implement SSH securely and efficiently and unlock the full potential of your linux device with remote access via ssh without setting port forwarding in your router.


Detail Author:
- Name : Dr. Lennie O'Keefe
- Username : meichmann
- Email : leonie.bartell@yahoo.com
- Birthdate : 1991-02-09
- Address : 472 Ledner Overpass Suite 778 New Abbie, WY 43234
- Phone : +14156218629
- Company : Cronin Ltd
- Job : Urban Planner
- Bio : Aut facere dolorem quaerat rerum quia eaque. Enim repellat accusantium voluptatem voluptate dignissimos sed unde.
Socials
linkedin:
- url : https://linkedin.com/in/nellesawayn
- username : nellesawayn
- bio : Nisi sapiente hic id nihil maiores labore.
- followers : 2567
- following : 1074
twitter:
- url : https://twitter.com/nelle_real
- username : nelle_real
- bio : Laudantium similique officiis numquam eos. Cupiditate perspiciatis minima ipsa nisi. Fuga quod et fuga non culpa qui. Ea officiis architecto vitae ea eos.
- followers : 1824
- following : 321
tiktok:
- url : https://tiktok.com/@nelle.sawayn
- username : nelle.sawayn
- bio : Voluptatem fugit beatae sed odit veritatis. Sed debitis quis est voluptatem.
- followers : 5174
- following : 2874