Secure SSH For IoT: Access & Protect Your Devices
Are your Internet of Things (IoT) devices truly secure? The escalating prevalence of remote access to IoT devices via Secure Shell (SSH) necessitates a proactive and informed approach to cybersecurity, making it paramount to understand and implement robust security measures to protect sensitive data and maintain operational integrity.
The landscape of the Internet of Things is vast and ever-expanding, with devices permeating nearly every facet of modern life, from smart home appliances to industrial control systems. As these devices become increasingly interconnected, the need for remote access and management grows exponentially. SSH provides a secure and efficient means to achieve this, but it also introduces potential vulnerabilities that malicious actors can exploit. Therefore, a deep understanding of SSH security best practices is crucial for safeguarding your IoT infrastructure.
The fundamental concept behind using SSH for remote access to IoT devices revolves around establishing a secure, encrypted connection between a client device and the IoT device. This is achieved through the SSH protocol, which ensures that all data transmitted between the two devices is protected from eavesdropping and tampering. SSH also provides a means of authenticating users, verifying their identity before granting access to the device. However, it is essential to remember that while SSH itself is secure, its implementation and configuration can significantly impact the overall security posture of your IoT environment. This is where the importance of password management, key-based authentication, and regular security audits comes into play.
- Unlocking Iot Your Guide To Device Management Security
- Best Remote Iot Platforms For Raspberry Pi A Comprehensive Guide
Implementing robust security measures isn't just about convenience; it's about safeguarding sensitive data and maintaining operational integrity. The convenience of remote access should never compromise the security of your IoT devices. Here's a deep dive into understanding the crucial elements of remote SSH login for IoT, ensuring the security of your devices while optimizing performance. This guide will walk you through the process, ensuring you have the expertise and tools needed to succeed.
Consider the implications of a compromised IoT device. Data breaches, system failures, and reputational damage are just a few of the potential consequences. The responsibility for securing these devices rests with those who deploy and manage them. This is why understanding the nuances of remote SSH login for IoT passwords is critical. The goal is to create a layered defense that minimizes the attack surface and protects against a variety of threats. One of the first steps in securing remote access via SSH is to change the default SSH password. For example, a Raspberry Pi comes with a default username "pi" and password "raspberry" for SSH access. Retaining these default credentials is akin to leaving the front door unlocked. It's an open invitation to anyone who wants to gain unauthorized access.
Security Considerations for SSH Remote Access
Here are some security considerations to keep in mind when using SSH for remote access to your IoT device:
- Change the default SSH password: As mentioned, default passwords are a primary target for attackers.
- Implement strong passwords: Use passwords that are long, complex, and unique to each device. Consider using a password manager.
- Disable password-based authentication (when possible): Favor key-based authentication for enhanced security.
- Use SSH key-based authentication: This is a more secure method than password authentication. If you do not have a key, create one, authorize this key on the remote host. From now on ssh user@ip will no longer ask for your password.
- Regularly update the SSH server software: Keep your SSH server software patched to address known vulnerabilities.
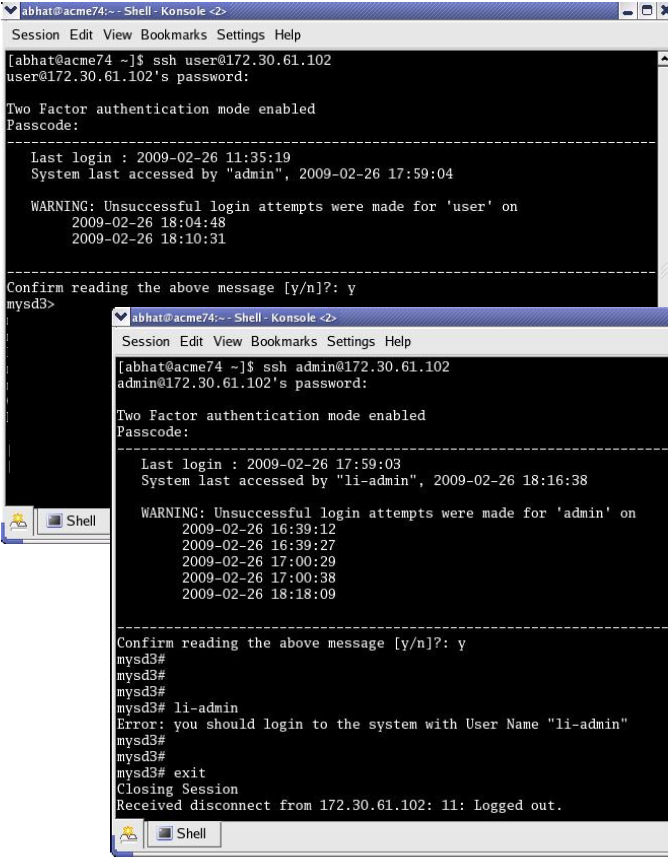
- Implement multi-factor authentication (MFA): Adding an extra layer of security, such as OTP or hardware tokens, further enhances authentication.
- Monitor SSH login attempts: Use logging and monitoring tools to detect and respond to suspicious activity.
- Restrict SSH access: Limit SSH access to authorized users and specific IP addresses or networks.
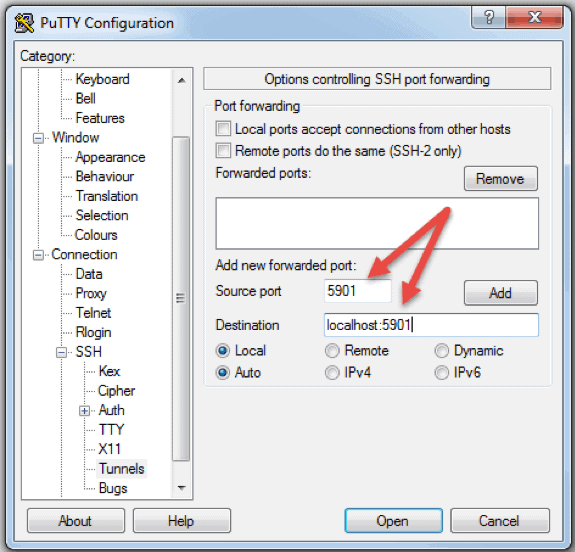
- Consider port forwarding: If you need to access internal services behind the firewall, use port forwarding through SSH.
- Review and update security policies: Regularly evaluate your security policies and make adjustments as needed.
Remote SSH login has become an essential tool for managing IoT devices securely and efficiently. As the internet of things continues to expand, understanding how to establish a secure connection through SSH is critical for maintaining device integrity and protecting sensitive data. Using SSH (secure shell) to log in to these devices from an Android device provides a secure and efficient way to manage them. Open your SSH client and enter the IP address of the IoT device, along with your username and password or SSH key for authentication. If everything is set up correctly, you should be able to establish a secure SSH connection to your device. Remote SSH login for IoT offers a free and secure solution for managing devices remotely. By understanding the fundamentals of SSH and implementing best practices, you can enhance the security and efficiency of your IoT projects.
Key-Based Authentication: The Preferred Approach
Key-based authentication represents a significant upgrade in security compared to password authentication. SSH keys are cryptographic key pairs: a private key that is kept secret by the user and a public key that is placed on the remote server. When a user attempts to connect to the server, the server challenges the user by requesting proof that they possess the corresponding private key. This eliminates the need for passwords, reducing the risk of brute-force attacks and credential theft. If you do not have a key, create one. Then, authorize this key on the remote host.
Heres a basic process:
- Generate an SSH Key Pair: On your local machine (the one you'll use to connect to the IoT device), use the `ssh-keygen` command to generate a key pair. This will typically create a private key (usually named `id_rsa`) and a public key (`id_rsa.pub`).
- Copy the Public Key: Copy the content of the public key file ( `id_rsa.pub`).
- Authorize the Key on the IoT Device: Log in to your IoT device (using the current password or the default ones) and navigate to the `.ssh` directory in the user's home directory. If the directory doesn't exist, create it. Create or edit the `authorized_keys` file within the `.ssh` directory. Paste the contents of your public key into this file, ensuring that each key is on a new line.
- Disable Password Authentication (Highly Recommended): Once key-based authentication is working, disable password authentication in the SSH configuration file on the IoT device (typically `/etc/ssh/sshd_config`). Look for the `PasswordAuthentication` option and set it to `no`. Restart the SSH service for the changes to take effect.
- Connect using SSH Key: From your local machine, you should now be able to connect to your IoT device using `ssh user@ip_address`. You will no longer be prompted for a password (provided your key is properly configured).
Best Practices for Secure Remote Access
Disabling password-based SSH authentication and enabling SSH key-based authentication for SSH login significantly improves IoT device remote access security. Openssh server and client software, combined with the power of SocketXP IoT remote access solution is a great combination for managing and maintaining your IoT device fleet remotely.
Beyond key-based authentication and strong passwords, here are further recommendations to harden your SSH configuration:
- Regularly Update OpenSSH: Keep your OpenSSH server and client software up-to-date. Patches often address security vulnerabilities.
- Use a Firewall: Implement a firewall on your IoT devices to restrict access to SSH and other services. Only allow connections from trusted IP addresses.
- Port Forwarding with Caution: While port forwarding through SSH can be convenient, use it judiciously. Carefully consider the security implications and only forward the necessary ports.
- Disable Root Login: Disable the ability to log in directly as the root user via SSH. This prevents attackers from immediately gaining privileged access if they compromise a user account.
- Change the SSH Port: By default, SSH listens on port 22. Change this to a non-standard port. This is not a foolproof security measure, but it can help to reduce automated attacks.
- Monitor SSH Logs: Regularly review SSH logs for suspicious activity, such as failed login attempts or unauthorized access.
- Implement Two-Factor Authentication (2FA): Adding 2FA, such as Time-Based One-Time Passwords (TOTP) or hardware security keys, significantly strengthens authentication.
- Regular Security Audits: Conduct regular security audits of your SSH configuration and IoT devices to identify and address potential vulnerabilities.
In short, an SSH IoT remote connection is vulnerable to security threats, but the right security measures can minimize the chances of security breaches. Remote SSH login IoT password management is not just about convenience; it's about safeguarding sensitive data and maintaining operational integrity. In todays interconnected world, managing remote SSH login IoT passwords has become a critical aspect of ensuring the security and functionality of IoT devices. These resources provide comprehensive guides and tutorials to help you master remote SSH login for IoT.
Leveraging Third-Party Solutions
Tools like SocketXP offer comprehensive solutions for managing SSH access to IoT devices. They streamline the process of establishing secure connections, automating tasks like key management, and providing centralized control over your IoT device fleet.
Follow these steps to setup SocketXP IoT agent and remote SSH into your IoT using SocketXP IoT remote access solution.
- Download and install the SocketXP IoT agent on your IoT device first.
- Configure the agent.
- Use the SocketXP dashboard or command-line tools to initiate an SSH connection to your device.
We will also show you how to securely transfer files to and from your devices using sftp/scp client tools.
Transferring Files Securely (SFTP/SCP)
In addition to SSH access, you'll often need to transfer files to and from your IoT devices. Secure File Transfer Protocol (SFTP) and Secure Copy Protocol (SCP) are designed for this purpose, providing secure and encrypted file transfer capabilities. SFTP is often the preferred choice, as it offers more advanced features and greater flexibility. The following is a brief guide:
- SFTP: Most SSH servers support SFTP. You can use SFTP clients (like FileZilla, Cyberduck, or the built-in SFTP client in many IDEs) to connect to your IoT device using your SSH credentials. After connecting you will then be able to securely transfer files to and from your device.
- SCP: SCP is a command-line tool that allows you to copy files securely. The basic syntax is `scp [source] [user@ip_address:destination]`.
These tools leverage the same SSH keys and security mechanisms as SSH login, ensuring that your file transfers are protected from eavesdropping and tampering. These secure file transfer methods are essential for tasks like deploying software updates, transferring configuration files, and backing up data.
Conclusion
Mastering secure remote SSH login for IoT devices is no longer optional; it's a critical requirement. It's a multifaceted approach requiring diligence and a continuous commitment to security best practices. By taking a proactive approach to password management, key-based authentication, regular updates, and monitoring, you can significantly enhance the security of your IoT projects.

Detail Author:
- Name : Sadye White
- Username : kledner
- Email : brook43@gmail.com
- Birthdate : 1993-12-15
- Address : 86629 Henri Expressway Apt. 286 West Rosie, SD 62727
- Phone : +15626402539
- Company : Konopelski-Crist
- Job : Assessor
- Bio : Necessitatibus voluptas nostrum natus enim nisi voluptas. Iure sapiente eum sint aut magnam tenetur molestiae. Reprehenderit minima aliquid architecto culpa.
Socials
facebook:
- url : https://facebook.com/emanuelschaden
- username : emanuelschaden
- bio : Quisquam officiis quisquam fugit aut et ut iure.
- followers : 1227
- following : 1912
twitter:
- url : https://twitter.com/emanuel7948
- username : emanuel7948
- bio : Sit laborum voluptas minus recusandae iste. Ut qui inventore explicabo omnis.
- followers : 5955
- following : 2622
instagram:
- url : https://instagram.com/emanuel.schaden
- username : emanuel.schaden
- bio : Et aspernatur repellat et est ea natus maxime soluta. Quia maxime saepe odit odio quis.
- followers : 4425
- following : 1704
linkedin:
- url : https://linkedin.com/in/schaden1974
- username : schaden1974
- bio : Libero nulla eaque error dolorem.
- followers : 1839
- following : 17
tiktok:
- url : https://tiktok.com/@schadene
- username : schadene
- bio : Et ducimus ad dolorem mollitia rem asperiores tempora nostrum.
- followers : 887
- following : 1696